In this area of cybersecurity, understanding various methods of how attacks get propagated is key to the protection of sensitive information. Amongst some of the most insidious approaches are spear phishing approaches that make use of personal relationships and the trust that people have for others to beguile targets to divulge confidential information. This article takes a close look at what spear phishing is in cybersecurity, how it works, the implications, and how one can prevent these attacks.
Defining Spear Phishing
What is Spear phishing in cyber security? Spear phishing is a kind of phishing attack that involves an individual or organization, and is mostly based on personal information to make it illegitimate. Unlike common phishing, spear phishing focuses on certain groups or even a particular person; hence, it is much more dangerous and effective as compared to common phishing attacks.
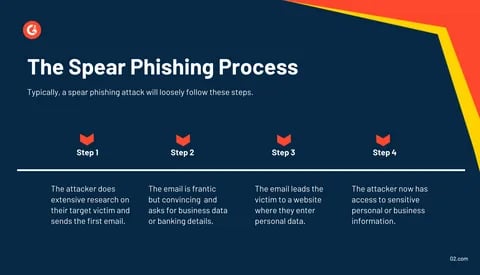
A spear phishing attack usually begins with detailed research into the target. According to experts, the attackers get their information from social media profiles, a company website, and public databases. With such knowledge about the target’s interests, relationships, and professional background, attackers can write very persuasive messages that cannot be easily differentiated from legitimate communications.
How Spear Phishing Works
The mechanics of how spear phishing attacks work typically follow these steps:
Target Identification: Here, attackers choose targets based on their job functions, access to sensitive information, or even a place in an organization. High-end executives turn out to be primary targets too because they have access to critical data.
Information Gathering and Reconnaissance: A hacker, after choosing a target, will not stop until he knows more personal information about the target, including names, e-mail addresses, places of work, and personal interests. Social networking sites, like LinkedIn and Facebook, enable this level of reconnaissance.
Crafting the Message: Using information obtained, the attacker will compose an individually personalized email or message that appears to come from a source with which the target trusts-a coworker or business partner. It may include particularized pieces of information so that the connection to the mark is made real and the compliance demand is pretty much assured.
Call to action: The mail often includes a call to action, such as checking on the link or opening the attachment; this triggers the execution of malware and theft of information. In this regard, for example, an attacker uses the disguise of the executive to plead for urgent financial information.
Exploitation: When the target falls into a trap and performs the desired action, the attacker obtains sensitive information or access to systems that can be used to obtain further financial benefit or as part of further attacks. The Impact of Spear Phishing The aftermath of spear phishing attacks could be disastrous for individuals and organizations alike:
Data Breach: A successful spear phishing attack may result in unauthorized access to sensitive data, leading to huge financial loss and damage to the reputation of an organization.
Identity Theft: Through spear phishing, personal information may be retrieved and availed for identity theft purposes, thereby resulting in fraudulent activities haunting a victim for many years.
Operational Disruption: Cybercriminals may plant malware to disrupt normal operations, and the downtimes create a loss of productivity.
Loss of Trust: Spear phishing attacks deal organizations a blow; they thus are at the mercy of their clients and investors, thereby losing trust in them for future business opportunities.
Prevention Strategies
Spear phishing attacks being of such a sophisticated nature, organizations have to put quite robust measures in place.
Security Awareness Training: It is highly recommended to train the employees through spear phishing tactics. Regular sessions will help staff recognize suspicious emails and check verification before taking action.
Solution for Email Filtering: Advanced systems in filtering email can be implemented that help in identifying and blocking all spear phishing emails before they reach the user’s inbox. These solutions normally make use of machine learning algorithms to analyze anomalies in email behavior.
Multi-Factor Authentication: MFA would serve as an additional layer of security since sensitive systems/data are accessed only when multiple means of verification have been provided.
Enforcement of Periodic Software Updates: Whatever software is in use or is under development should receive periodic updates so their vulnerabilities may be identified and taken care of in due time, hence reducing spear phishing attacks.
Incident Response Plans: The organization should have well-charted-out incident response plans in case such breaches happen for quick and efficient response.
Simulated Phishing Tests: Regular simulated phishing tests will always reflect the real scenery of an organization as to where the employees stand in terms of preparedness and awareness regarding a spear phishing attack. These fortify training and point out areas where the weaknesses lie.
Conclusion
Understanding what spear phishing is in cybersecurity gives meaning to personal or organizational defense. Once stakeholders are aware of the tactics that hackers use to get into their target’s system, then informed stakeholders can take necessary measures to reduce their vulnerability.
Along with advancing technology, cyber threats have become more challenging than ever. Thus, it will be essential to learn new tactics such as spear phishing to maintain a strong security posture. Education, awareness, and preventive measures will be the best antidotes to this evil growing very rapidly in today’s digital arena of spear phishing.